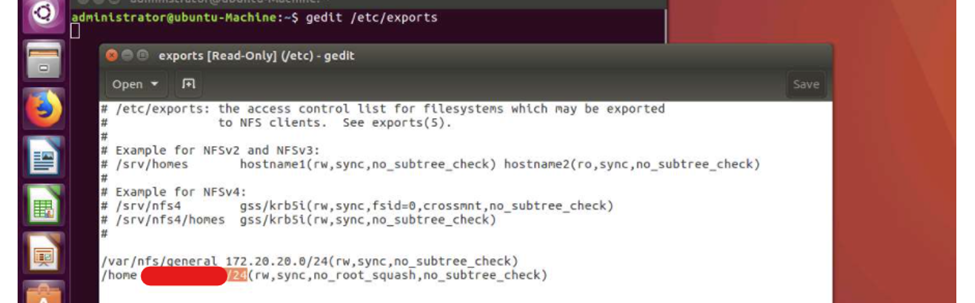
From the Qterminal in a Kali machine, the following line of code can be executed to check the vulnerabilities associated with the version of Owncloud that is being used.
:~# searchsploit ownCloud [version]Then it is likely to receive as a response the name of a file that contains the possible vulnerabilities. Now, after getting that name, we need to know the path of this file
:~#searchsploit -p file_nameTo examine the txt file:
:~#leafpad [path of the file]It is possible to find the proof concept and then try to exploit this vulnerability
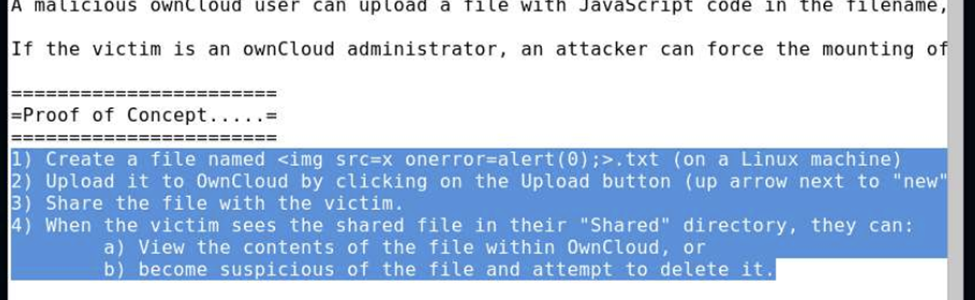
So basically, by creating and sharing a txt file with the name [<img src=x onerror=alert(0);>.txt] the file will return an alert pop-up with a value “0“ every time the victim tries to delete or view it. This opens up the possibility of a cross-site scripting attack on the ownCloud Application.